A contractor working for cell giant Sprint stored on an unprotected cloud server hundreds of thousands of cell phone bills of AT&T, Verizon and T-Mobile subscribers.
The storage bucket had more than 261,300 documents, the vast majority of which were phone bills belonging to cell subscribers dating as far back as 2015. But the bucket, hosted on Amazon Web Services (AWS), was not protected with a password, allowing anyone to access the data inside.
It’s not known how long the bucket was exposed.
The bills — which contained names, addresses and phone numbers, and many included call histories — were collected as part of an offer to allow cell subscribers to switch to Sprint, according to Sprint-branded documents found on the server. The documents explained how the cell giant would pay for the subscriber’s early termination fee to break their current cell service contract, a common sales tactic used by cell providers.
In some cases we found other sensitive documents, such as a bank statement, and a screenshot of a web page that had subscribers’ online usernames, passwords and account PINs — which in combination could allow access to a customer’s account.
U.K.-based penetration testing company Fidus Information Security found the exposed data, but it wasn’t immediately clear who owned the bucket. Fidus disclosed the security lapse to Amazon, which informed the customer of the exposure — without naming them. The bucket was subsequently shut down.
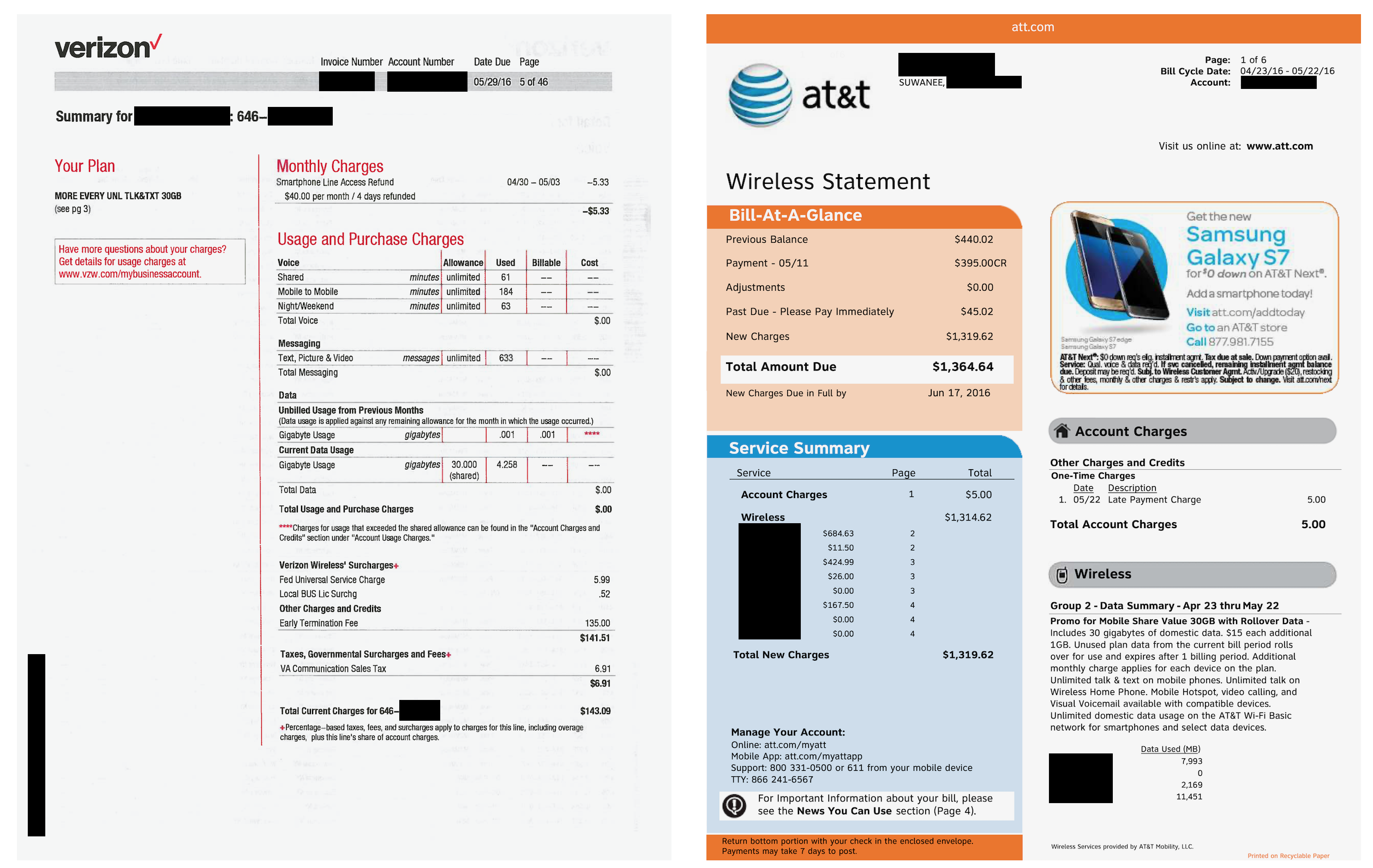
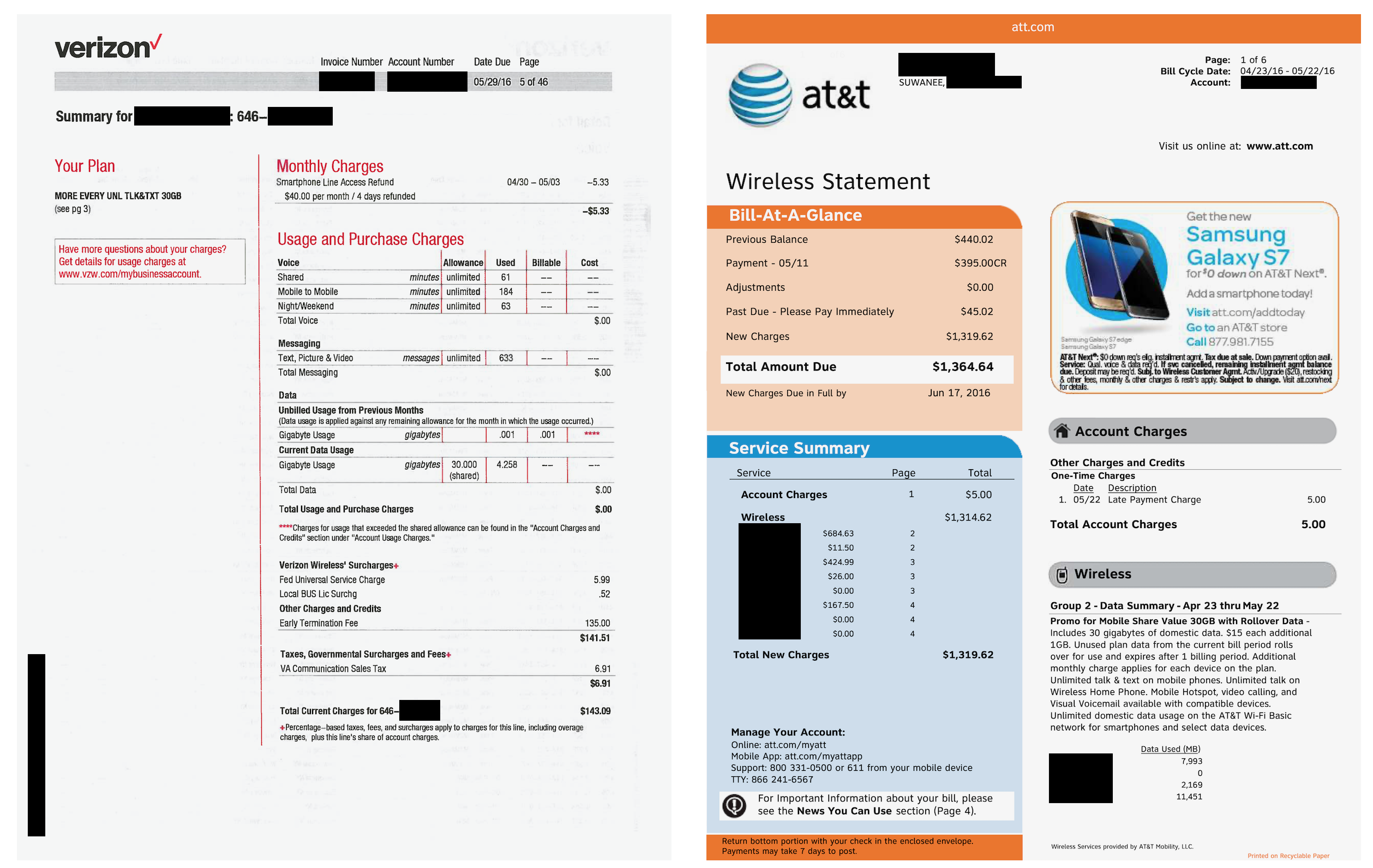
A Verizon and AT&T phone bill from two customers. (Image: supplied)
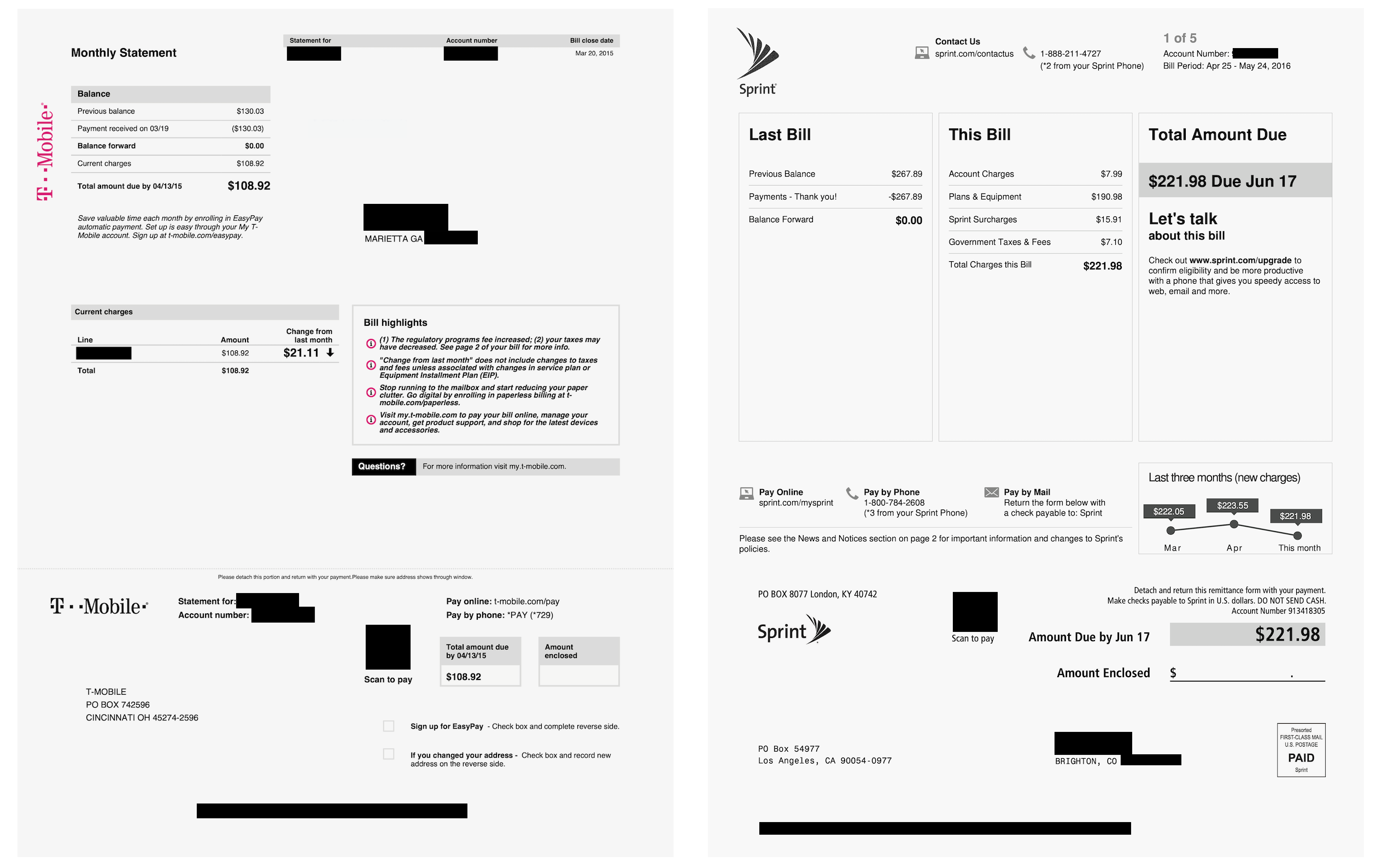
A T-Mobile bill found on the exposed servers. A handful of Sprint bills were also found. (Image: supplied)
After a brief review of the cache, we found one document that said, simply, “TEST.” When we ran the file through a metadata checker, it revealed the name of the person who created the document — an account executive at Deardorff Communications, the marketing agency tasked with the Sprint promotion.
When reached, Jeff Deardorff, president of Deardorff Communications, confirmed his company owned the bucket and that access was restricted earlier on Wednesday.
“I have launched an internal investigation to determine the root cause of this issue, and we are also reviewing our policies and procedures to make sure something like this doesn’t happen again,” he told TechCrunch in an email.
Given the exposed information involved customers of the big four cell giants, we contacted each company. AT&T did not comment, and T-Mobile did not respond to a request for comment. Verizon spokesperson Richard Young said the company was “currently reviewing” the matter and would have details “as soon as it’s available.” (TechCrunch is owned by Verizon.)
When reached, a spokesperson for Sprint would not disclose the nature of its relationship with Deardorff nor would they comment on the record at the time of writing.
It’s not known why the data was exposed in the first place. It’s not uncommon for AWS storage buckets to be misconfigured by being set to “public” and not “private.”
“The uptrend we’re seeing in sensitive data being publicly accessible is concerning, despite Amazon releasing tools to help combat this,” said Harriet Lester, director of research and development at Fidus. “This scenario was slightly different to usual as it was tricky to identify the owner of the bucket, but thankfully the security team at AWS were able to pass the report on to the owner within hours and public access was shut down soon after.”
We asked Deardorff if his company plans to inform those whose information was exposed by the security lapse. We did not immediately receive a response.
Read more:
- Tuft & Needle exposed thousands of customer shipping labels
- StockX was hacked, exposing millions of customers’ data
- DoorDash confirms data breach affected 4.9 million customers, workers and merchants
- Equifax breach was ‘entirely preventable’ had it used basic security measures, says House report
- Stop saying, ‘We take your privacy and security seriously’
- Capital One breach also hit other major companies, say researchers
- Macy’s said hackers stole customer credit cards — again