This story was delivered to BI Intelligence “Payments Briefing” subscribers. To learn more and subscribe, please click here.
Verifone controllers at approximately two dozen gas station convenience stores were targeted by an intrusion in January, security blog Krebs on Security reports.
As a titan in payment terminal manufacturing, operating in 150 countries and counting 5,000 employees, news of Verifone’s breach is sure to attract heavy scrutiny. Past large scale breaches involving Target and Home Depot data breaches have brought widespread attention to the incidents. Here’s what’s known about the Verifone attack:
- The extent of the breach is reportedly contained. Verifone commented that they “believe” the duration of the attack was short, the extent was limited to its corporate network, no other merchants were affected, and the integrity of their networks and terminals remains intact, in a statement reported by Krebs. The card terminal manufacturer said that it quickly notified card network partners like Visa and Mastercard, had employees reset passwords, and brought in a third-party forensic team.
- The type of data affected hinges on Verifone’s defenses. Details on how the attack took place are not yet available, though an internal Verifone memo attributed an “IT control issue.” Lack of clarity around the origin and the extent of the attack means that the impact isn’t entirely clear. Shane Stevens, VASCO Data Security’s director of omnichannel identity and trust solutions told BI Intelligence that the type of data collected is dependent upon Verifone’s infrastructure setup and anti-fraud defense mechanisms, like “network segregation, continuous data encryption, and strong credentialing on applications.”
No adverse effects or misuse of data has been detected from this event — yet . Speculating on Verifone’s worst possible outcome, Krebs quoted a Avivah Litan, a Gartner analyst who noted the attackers may have stolen information about Verifone’s POS systems to create backdoors that “record, store and transmit stolen customer card data.” Though it’s unclear what type of data may have been compromised, Stevens told BI Intelligence that the best-case scenario is that just company passwords and nothing more were impacted during or after the breach, but that results remain to be seen.
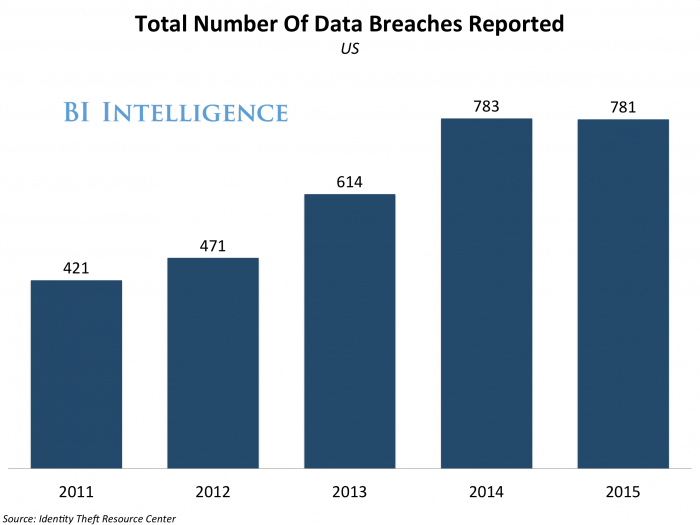
It’s no surprise that companies are more worried than ever about the looming threat of hackers penetrating their networks. In the last year, the number of records exposed in data breaches rose 97%, according to the Identity Theft Resource Center.
The frequency and sophistication of cyber attacks are at an all-time high, and the costs associated with data breaches continue to rise. While companies are investing more in cybersecurity to ward off attacks, they know they won’t be able to spend their way to absolute security. A cybersecurity team of more than 1,000 staffers with a budget of $250 million wasn’t enough to save JPMorgan Chase from getting hacked in 2014. As a result, companies are turning to cyber insurance to help mitigate the costs of a potential breach.
However, insurers have been slow to extend cyber insurance to many businesses, as they have yet to develop proven tools to help them assess the risks and costs associated with cyber attacks. Cyber insurance policies also often have high premiums and low coverage limits to help protect insurers from incurring too much exposure to a cyber attack.
BI Intelligence, Business Insider’s premium research service, has compiled a detailed report on cyber insurance that examines the growth of this market and identifies the key factors driving that growth. It also identifies the commercial sectors that are underserved in the cyber insurance market, which present a unique opportunity to insurers. Finally, it explains how insurers can find creative ways to cover these underserved markets while still limiting their overall exposure.
Here are some key takeaways from the report:
- Cyber insurance plans cover a variety of costs related to cyber attacks, including revenue lost from downtime, notifying customers impacted by a data breach, and providing identity theft protection for such customers.
- Annual cyber insurance premiums will more than double over the next four years, growing from to ~$8 billion in 2020.
- However, many insurance companies have been hesitant to offer cyber insurance because of the high frequency of cyber attacks and their steep costs. For example, Target’s notorious data breach cost the company more than $260 million.
- Insurers also don’t have enough historical data about cyber attacks to help them fully understand their risks and exposures.
- There are large underserved markets with very low cyber insurance adoption rates such as the manufacturing sector, where less than 5% of businesses have cyber insurance coverage.
In full, the report:
- Projects the growing demand and premiums for cyber insurance in comparison to other common forms of commercial insurance.
- Illustrates how cyber attacks are growing more sophisticated and more costly, which is driving more companies to consider cyber insurance.
- Explains the obstacles that insurers face in extending cyber insurance coverage to different types of businesses.
- Provides insights on how insurers can overcome these challenges to grow their cyber insurance business without incurring too much risk.
To get your copy of this invaluable guide to cyber insurance, choose one of these options:
- Purchase an ALL-ACCESS Membership that entitles you to immediate access to not only this report, but also dozens of other research reports, subscriptions to all 5 of the BI Intelligence daily newsletters, and much more. >> START A MEMBERSHIP
- Purchase the report and download it immediately from our research store. >> BUY THE REPORT
The choice is yours. But however you decide to acquire this report, you’ve given yourself a powerful advantage in your understanding of cybersecurity.
Learn more:
- Credit Card Industry and Market
- Mobile Payment Technologies
- Mobile Payments Industry
- Mobile Payment Market, Trends and Adoption
- Credit Card Processing Industry
- List of Credit Card Processing Companies
- List of Credit Card Processing Networks
- List of Payment Gateway Providers
- M-Commerce: Mobile Shopping Trends
- E-Commerce Payment Technologies and Trends